The Impact of Regulatory Compliance on the Cybersecurity of Energy Utilities – An American View
From the early days of relying solely on IT departments to deploy, configure, and maintain cybersecurity solutions, organizations are now adopting a culture of compliance in which everyone has a role to play in keeping systems and networks secure. What has been the impact of regulations on this change and are energy utilities better protected today against cyber-attacks?
Over the past two decades
Over the past two decades, critical industries have progressively adopted stricter cybersecurity regulations to address an onslaught of compromises, data leaks, and, more recently, ransomware. The Sarbanes-Oxley Act (SOX) was enacted in July 2002 in the United States following a period of corporate scandals (e.g., Enron and WorldCom) to restore investors’ confidence in the financial markets and close loopholes that allowed public companies to defraud investors. The implementation of SOX Form 302 (corporate responsibility for financial reports) and Form 404 (management of internal controls) added key requirements to cyber risk disclosures. This was followed a few years later by the payment credit card industry that introduced mandatory compliance called PCI-DSS for every merchant processing credit or debit card payments.
The main purpose of PCI-DSS has been to reduce the risk of payment data loss by enforcing protection and encryption of card information in transit through networks and at rest in databases and systems. In 2008, the North American Reliability Corporation’s Critical Infrastructure Protection standards (NERC CIP) was launched to protect, secure and maintain the North American electrical grid in the face of increasing cyber risks. The equivalent in Europe is the Network and Information Security (NIS) directive that was adopted in 2016 with the goal of enhancing cybersecurity for member states through a combination of EU-wide legislation, cross-border collaboration, and specific national capabilities.
Author
Don Miller & Robin Berthier
Network Perception
About
Cybersecurity of Energy Utilities.
Cybersecurity
Global spending on cybersecurity doubled between 2011 and 2016 and has continued to rise. The impact of cybersecurity standards has played a significant role in those budget increase and we are interested in understanding the following core questions:
- Has cybersecurity regulation made our environments more complex and has it driven innovation?
- Have regulatory standards effectively decreased cybersecurity fraud and breaches?
- Has regulation increased costs or provided saving opportunities?
An initial review of data breaches over the past 10 years indicate that an increasing volume of records get compromised every year and the average cost of a large data breach (defined as a data theft in which at least 30,000 records were compromised) has reached $150 million in 2020. Beyond exploiting security vulnerabilities in software, the main reasons organizations get successfully compromised are (1) due to accidental or intentional misconfigurations of software and (2) lack of oversight on environments and changes made to systems and networks. These are two areas specifically covered by cybersecurity regulations. Would the continuous increase of significant incidents indicate that standards are falling short in improving the security of organizations?
Electric utility industry
A closer look at the specific case of the electric utility industry in the US and the NERC CIP standards that have been implemented since 2011 shows a different takeaway. While publicly available data on cyber incidents occurring in critical infrastructure is hardly available, we can look at the evolution of NERC CIP violations over time to get a sense of security preparedness. The figure below shows that from a high of more than 1,000 violations recorded in 2012 (the first full year of enforcement), the number of violations has been reduced by more than 60% in just 4 years, indicating that electric utilities have taken the regulatory rules seriously and have adopted a culture of compliance to closely follow the standards in their critical environments.
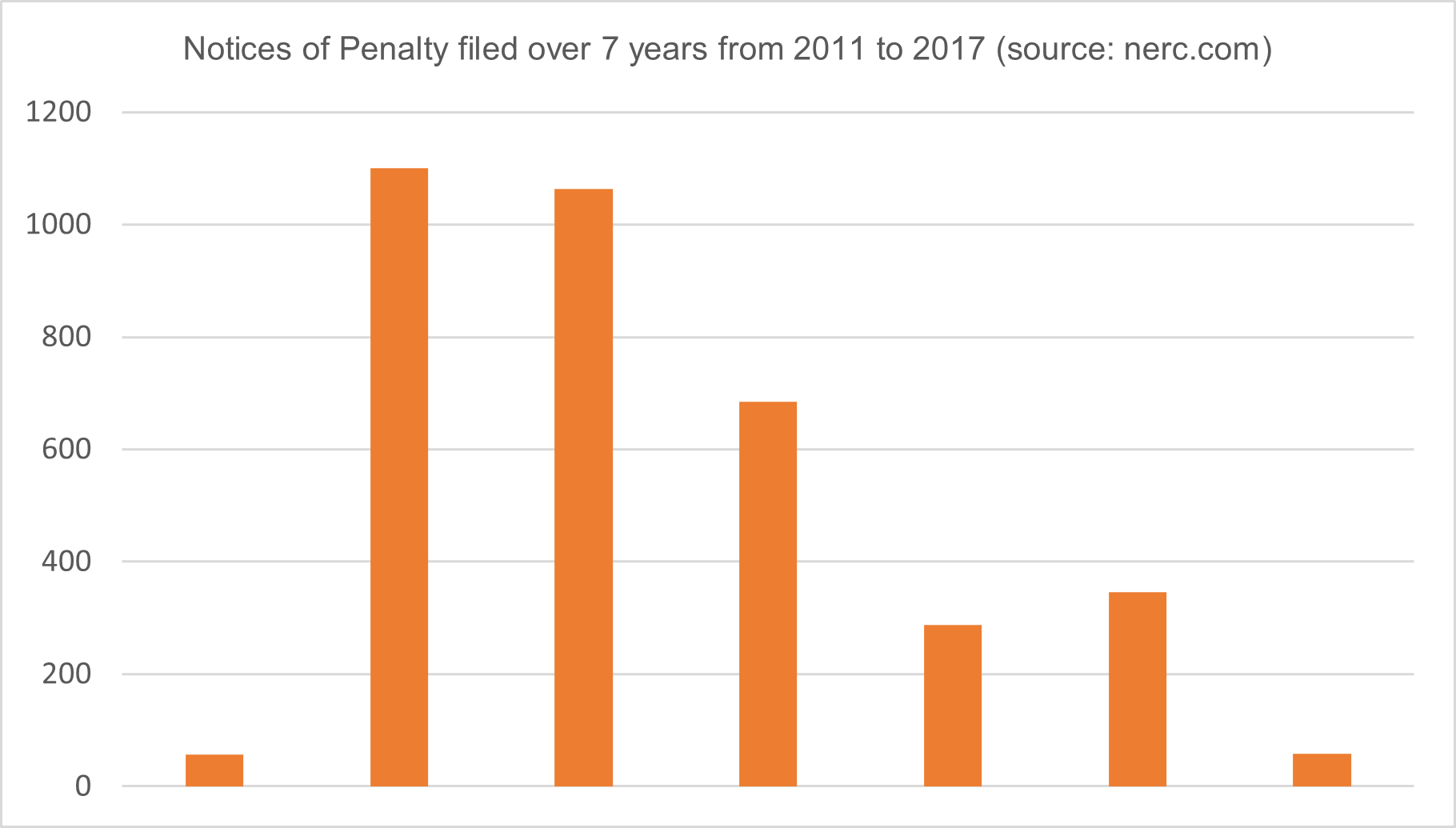
Indeed, we see CIP standards being implemented and managed across organizations through multiple stakeholders including cybersecurity teams, asset owners, compliance teams and senior management. In addition to these team, consultants and vendors have also become part of the adoption of compliance through the development of best practices, services, and software solutions to create transparency and make implementation and auditing much easier.
In conclusion
In conclusion, while cyber-attacks continue to rise, and our environments continue to get more complex, electric utilities are better prepared today thanks in part to cybersecurity standards. An ecosystem of internal and external auditors, compliance groups, and government orders have increased oversight and enabled larger budgets to be allocated for cybersecurity and IT/OT teams to implement appropriate security controls. We have witnessed the creation of new businesses and dedicated working groups with the same objective to protect our critical assets. Software development teams have also introduced new solutions to automate controls to adhere to requirements. In addition, knowledge among organizations on how to best secure their environments are better shared today thanks to efforts by the Department of Homeland Security (DHS), the E-ISAC in the US, the CSIRTs Network in Europe, and professional conferences such as NERC GridSecCon.
We recommend utilities to start with establishing a risk management strategy at the top level of the organization before business process and information technology. This strategy should provide an approach for risk prioritization that include consideration of impact. Frameworks to guide this process include the Cybersecurity Capability Maturity Model (C2M2) Program and the Cybersecurity Risk Management Process (RMP) from the U.S. Department of Energy, the National Institute of Standards and Technology cyber security framework (NIST CSF), and the ENISA CSIRT maturity assessment model that leverages the Security Incident Management Maturity Model (SIM3). Once a strategy has been defined at the top level, it can be expanded for the business and technology areas of the organization. It is also important to define a process to periodically update the risk management strategy, so it reflects the current threat and compliance environment.
About the authors

Donald Miller
Donald Miller is is the Technology Evangelist at Network Perception and a 25 year veteran of the cybersecurity, compliance and utility industry. Previously, he was Director of Management Consulting at SecureState LLC and responsible for delivering cyber security strategies and compliance with regulatory standards such as Sarbanes Oxley, Critical Infrastructure Protection. He was also the Manager of Cyber Security and Compliance at FirstEnergy Corporation for 15 years, responsible for all cyber and compliance programs that met CIP, Sox, and FERC for the corporation. Donald Miller holds a Bachelor of Science degree in Technology, a Master’s degree in Computer Science and an Executive MBA from Kent State University.

Robin Berthier
Dr Robin Berthier is the co-founder and CEO of Network Perception. He has over 15 years experience in the design and development of network security technologies. He was part of the University of Illinois research team that originally developed the technology that drives the Network Perception Platform. He received his PhD in the field of cybersecurity from the University of Maryland College Park before joining the Information Trust Institute (ITI) at the University of Illinois at Urbana-Champaign (UIUC) as a Research Scientist.
Network Perception was launched in 2014 at the University of Illinois at Urbana-Champaign Research Park. Founded by a team of experts on network security and critical infrastructure protection, Network Perception delivers a pioneering solution that enables corporate compliance and cyber security managers to gain a complete view of their network security and to immediately determine if its configuration is in alignment with best practices and regulatory standards.


